For the past decade, the growth of social media platforms have been enormous. These platforms are used to connect and create relationships with friends and people that we interact with on a daily basis. Even though these social networks are meant for people to add their friends, it turns out that these platforms are very susceptible to attackers that are looking to send spam for their personal gain. But, how do these attackers get the opportunity to include themselves in a network of friends that they do not belong in? Using Facebook as a common social network, have you ever received a friend request from a random person? This is exactly the way these attackers get themselves involved within a network. All it takes is one friend of a large network of friends to accept that request from the attacker that will now allow the attacker a path to all other members of the large network. If you have any personal information such as your phone number or email on your profile, these will now all be compromised and make you vulnerable to spam attacks. Because of the undirected nature of these friend relationships, mindlessly accepting requests on these social networks will leave you exposed to such attacks.
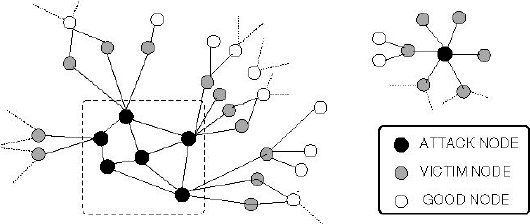
If we think of this in terms of what we know about networks, this is an extremely common occurrence. Once a user forms a friend relationship with an attacker, this can be seen as a bridge edge from a group of attackers to a group of normal friends. Another aspect of social networks is the concept of mutual friends. This initial relationship between one attacker and one real user can quickly snowball into further relationships between other attackers and other real users. Therefore, we now no longer have a single bridge node connecting these two groups of graphs, but several local bridges that strengthen their relationships that will lead to more attacks.
In conclusion, being apart of a social network can leave us vulnerable from attackers looking to send spam messages. The obvious solution to this is to avoid including personal information in our social media profiles. Other than this, we must be careful with who we decide to share our profiles with, as we could be creating a bridge between a network of attackers and our group of friends.
Reference
Shrivastava, N., Majumder, A., & Rastogi, R. (2008, April 12). Mining (Social) Network Graphs to Detect Random Link Attacks. Retrieved from https://ieeexplore.ieee.org/abstract/document/4497457.
