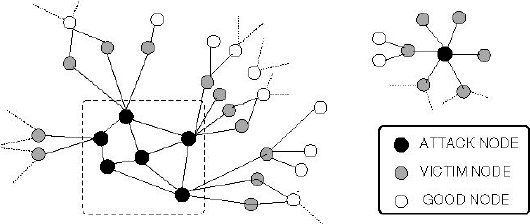
Recently, a new malware known as Nodersok/Divergent, surfaced. While the steps this malware takes to infect a system are an interesting topic to look into, that will not be the focus of this post. Rather we will look at what an infected system can do, within the network it is connected to.

The malware allows malicious JavaScript code to run and execute under the valid program Node.exe. The payload of the malware contains basic functions, which turns the infected machine into a proxy, accessible through a remote machine controlled by the attacker. While this does not give the attacker direct access to other machines on the network, there is still a breach within the infected PC’s network. An attacker can for example, use that machine as part of other malicious activities. Since the requests are being proxied through the infected machines, they may not necessarily be traced back to the attacker, but rather from the infected PC’s.
While the malware itself, turns machines into proxies, it is interesting to think about what security threats this may pose on its network, especially if this malware were to evolve. For example, take a machine that sits within an isolated network: or in terms of graphs, an isolated, disconnected SCC. Machines would only be accessible from other machines on the network. However, as soon as one machine becomes infected, it’s possible that the attacker now has access to information on other machines, as requests would come from the infected machine.
This leads to an interesting idea of how networks should be set up, in order to protect against threats such as this. For example, is it important and necessary to have all the machines in one SCC, or can some parts be even more isolated? If communication channels between the machines in the network are two-way (such as in an undirected graph), a possible solution could be to have one way communications between machines, similar to a directed graphs, in order to restrict the way machines can communicate. All in all, security breaches from malware related to networking requests, can pose a large threat, and should be taken into account when designing how machines are connected within a network.