Shopping for groceries is an extremely common practice that we go through multiple times a month. It is important that we find local grocery stores that are cheap to make our trips inexpensive. But, due to the low amount of competition in the industry, these retailers take advantage of the consumers by pricing items approximately the same in order to control the market and increase their profit. There are a lot of factors that goes into deciding how to price items to gain the maximum profit possible but Ezeala-Harrison and Baffoe-Bonnie both show that given two retail stores that belong in a regional oligopoly (few competition), if they both operated as rivals, the best choice for both of the stores would be to not co-operate with each other.
Consider the following payoff matrix:
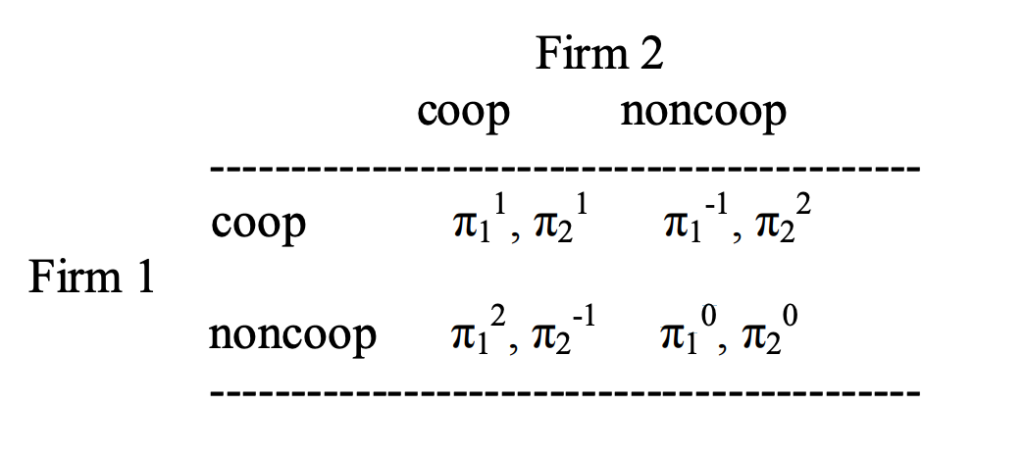
We will define “cooperate” as a store not playing any aggressive moves and “non-cooperate” as a store that is making aggressive decisions such as significantly altering prices of products that also belong to rivals. Considering the figure above, we can look at the power of each term to determine the payoff that the specific firm will receive (i.e power of 0 indicates breaking even while greater than 0 implies profit and less than 0 implies losing money). By observing the above figure, we can see that the Nash equilibrium of the decisions of these two firms is if they both do not co operate, implying a competitive environment where both stores are making aggressive actions. In the published paper, Ezeala-Harrison and Baffoe-Bonnie compute by probability, the best choice of both the firms which also concludes that both firms can establish greater benefits by not cooperating.
By our results of the payoff matrix above, we would expect that both firms that belong in an oligopoly would compete against each other aggressively, as it would give better results. In real life, this isn’t the case. There can be multiple reasons why the conclusions from the payoff matrix isn’t accurate (i.e various factors that go into choosing pricing for products) but the most likely cases are either 1) firms price match each other or 2) collusion between these firms. In an oligopoly market, the small amount of competition are given the opportunity to work together (sometimes illegally) in order to benefit all competition. This can involve both firms raising prices of the exact same products, leaving consumers no choice but to buy unreasonably priced groceries.
In conclusion, oligopoly markets involving the retail grocery industry exhibits behaviour that is not natural based on a simple Prisoners Dilemma model and indicates to us that price matching may occur between the firms in these markets or collusion with the stores exists. Either way, the local consumers unfortunately have to suffer consequences of buying overpriced products if they happen to live in regions dominated by few competition.
Reference
Ezeala-Harrison, F., & Baffoe-Bonnie, J. (2016, January 30). Market Concentration in the Grocery Retail Industry: Application of the Basic Prisoners’ Dilemma Model. Retrieved from http://www.scienpress.com/Upload/AMAE/Vol%206_1_3.pdf.