With the 2019 Federal Election having recently taken place, the idea of strategic voting was observed. Strategic voting is basically where someone may vote for a candidate whom they may not necessarily want to win, but is a better option that someone else winning. Someone may strategically choose to vote, if they believe their candidate does not have a chance of winning. For example, take three parties Conservatives, Liberals, and the Green Party. If someone wanted the Green party to win, but the Green party did not have a high chance of winning, that person may instead choose to vote for Liberals for example, if they did not want the conservatives to win. While strategic voting may not have been the driving force for all voter’s decisions, it is an interesting idea to take a look at applied on a large scale, such as voting.
Voter’s who strategically voted, instead of simply voting for the candidate they wanted to win without thinking about other possible options, demonstrate the idea of game theory. Based on the article, Liberals benefited the most from strategic voting, and as such a sample scenario with be outlined where Liberals benefit from strategic voting.
For example, say we Conservatives have 50% support, Liberals have 49% support, and Green Party has 1% support. Without strategic voting and assuming every voter votes for the party they support, conservatives will win since they have the most support. However, imagine green supporters realize their party will not win, and strategically vote instead. Assume in this example, the voter would prefer the Liberal party to win over Conservatives.
We can assign numbers to represent how happy a voter will be if a party is elected.
Voter 1 (Supports Green party) -> Conservative = -5, Liberal = 0, Green = +5
Voter 2 (Supports Conservatives) -> Conservative = +5, Liberal = -5, Green = 0
Furthermore, assume that the background colour of the box represents the party who wins (Blue being Conservative and Red being Liberals). We can then define the game as such:
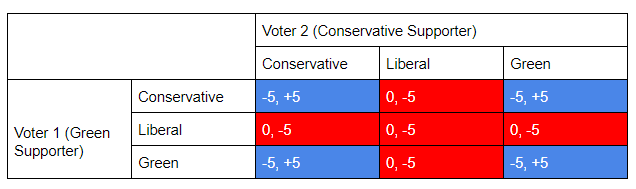
As we can see, a Conservative supporter will vote conservative, as their party does have a good chance of winning and therefore their vote will help conservatives win. However, a green party supporter who prefers Liberal over Conservative, may realize that voting Liberal instead of Green will be the better option. This is because as Green does not have a high chance of winning, and Liberal winning would be preferred over Conservatives winning.
Obviously the example outlined above, does not outline every possible scenario as there are other parties to consider, and the 2 voters can support different parties. Furthermore, not everyone will strategically vote. However, this does serve to outline how Game Theory applies to strategic voters, even if they may not be aware of it themselves.
References
https://nationalpost.com/news/politics/election-2019/liberals-benefited-most-from-strategic-voting-poll-of-late-deciding-voters-finds
https://www.cbc.ca/news/politics/poll-strategic-voting-1.5339692

