Recently, Instagram has removed two notable features from its app; the like counter, which displays the total number of likes of any given post, and the following page. This wasn’t due to the GDPR or any security or privacy concerns.
Rather, it is an attempt by Instagram (and Facebook) to counteract the popularity contests that exist all over social media. Consider influencers that hype up products. If they pay enough people to gain traction on their products, they will eventually gain many likes on their posts.
By applying the herd model, if you see that a post has been liked by many of your friends and has a extremely high like count, there is a very high percentage that you would also like this post, even if you are impartial to the actual content. Why? If the post is about something you are not familiar with, you would trust the post because of two factors:
- a high like count implies this post is trustworthy and many people like the content, so the content must be good
- friends believe it is also a good post, and you trust your friends
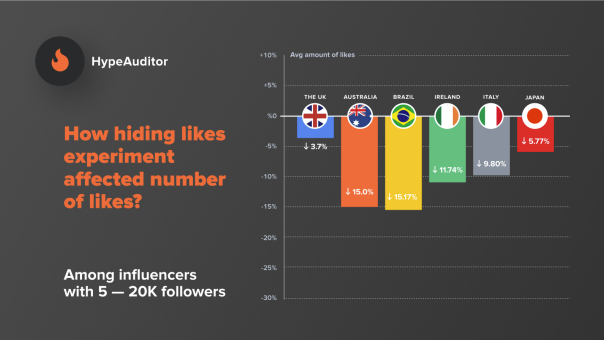
What Instagram has done partially shuts down herd mentality completely. For one, removing the like count on posts lowers the chances of information cascade because at first glance, it is difficult to tell how many people like and agree with the post (of course, Instagram still shows a list of all users that have liked the content, but it requires additional actions). As the user, you will be more likely to trust your own instinct and make your own decisions on the content of the post without being affected by what others have said (unlike the maj-colour urns) because you cannot see how many people “agree” with the post. Secondly, by removing the following page, it also prevents you from viewing what your friends have liked, which also reduces the chances of information cascade. Herd mentality is stronger when it involves people you know because there is more inherent trust. Lastly, this also counteracts the issue of botting (creating “robot” accounts that don’t follow a typical human’s usage) for likes, because increasing a hidden like counter provides no incentive for promoting a post, unless the content is well-liked.
This trend shows that more social media platforms should follow Instagram’s new model of hiding metrics that may encourage herd mentality so that people can express their true thoughts and feelings without being pressured socially by others. It encourages users to evaluate the information presented and respond appropriately.
Source: https://techcrunch.com/2019/11/14/instagram-private-like-counts/