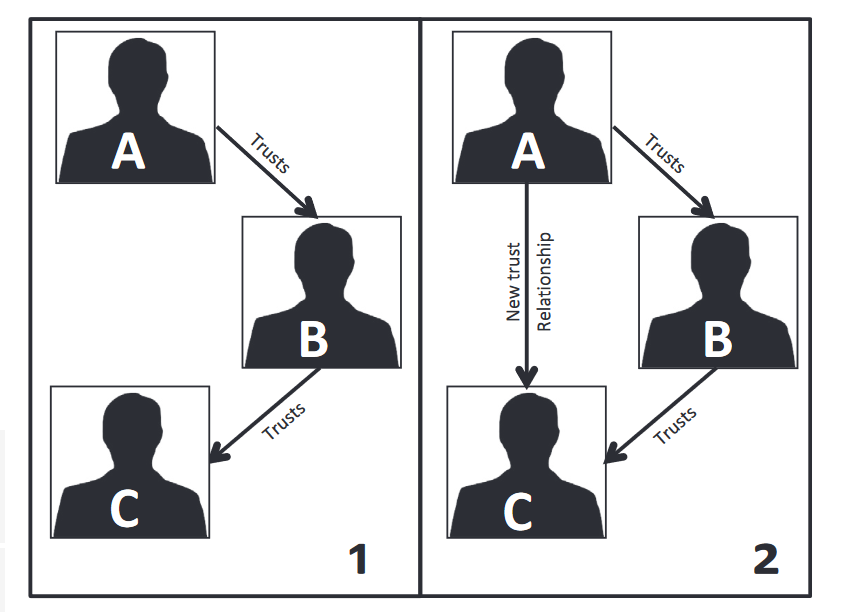
In today’s modern day, people are connected with other people; not just in school or at the workplace, but also on the Internet. There are various popular social applications such as Facebook, Twitter, and Instagram which allow us to get in touch with our friends. With the introduction of online dating in social networks, people are able to find romantic partners online in ways never imaginable before. However, the communication will be most likely happen on the Internet, which gives people the option to meet up in real life only if they are comfortable in doing so.
This topic is relevant to the study of Game Theory, which we covered in class with some examples about how two people (or groups) will select a strategy that provides the highest payoff or benefits. Most people, if they are rational, will choose the best strategy based on what other people choose (i.e. dominant strategy). In the perspective of dating app users, the following example below illustrates the mindset of when they engage in a conversation with another user, which relates very closely to the Prisoner’s dilemma that was also covered in class.
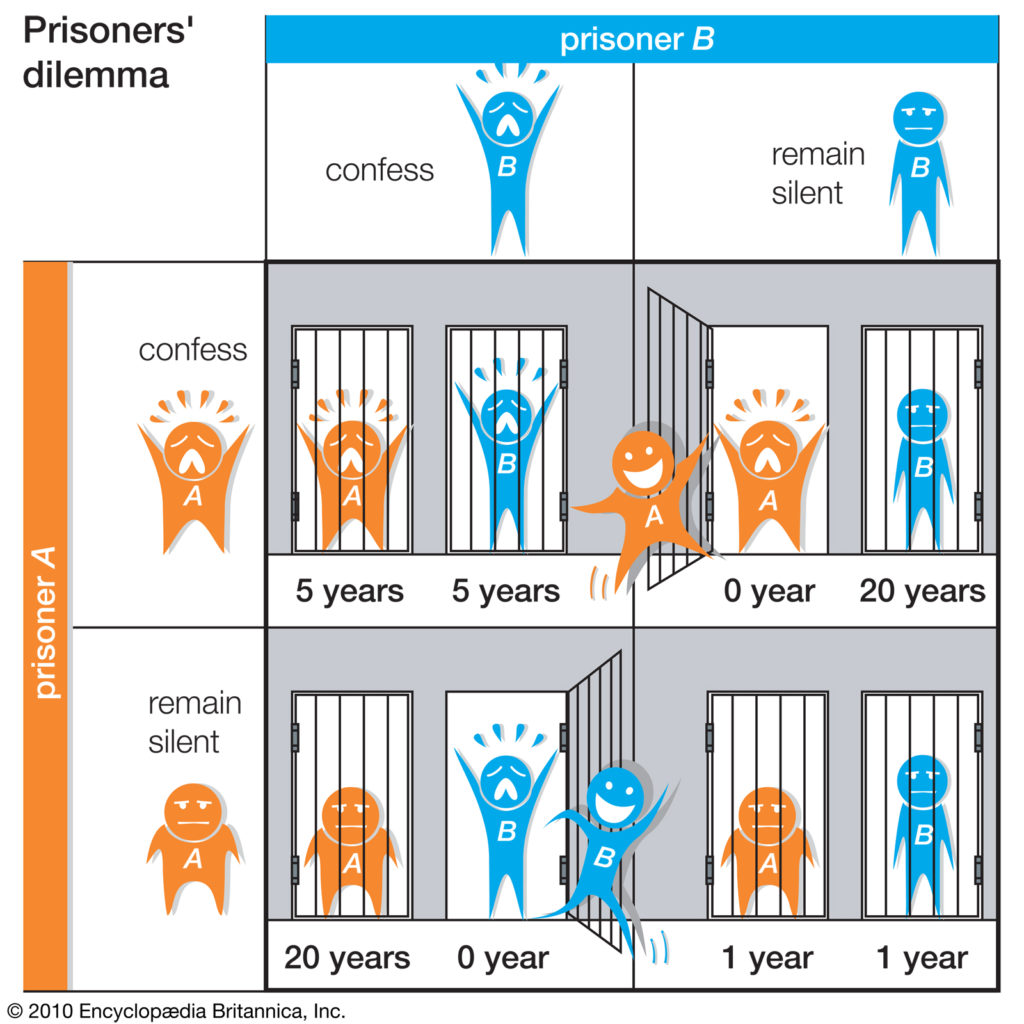
Alice and Bob are users on a dating application and they found each other on the application, wanting to know more about each other. Bob initiates the conversation and they both have a good time talking. Later on, they decide to go on a date, and it goes great. They both feel good about each other and they now like each other, but none of them have asked the other to confirm their current status. Moreover, they did not text each other after the date. After two days from the date, Bob finally decided to ask Alice if she wanted to hang out with him. He did not contact Alice after the date because he did not want to scare her away or seem too eager to start a relationship. When Alice received this message, she felt relieved since she was thinking why Bob did not text her after the date. She did not reply to Bob immediately, but after another two days. Alice made this decision because she also did not want to seem like she was being too eager to start a relationship.
From the example above, we can see that dating is a strategy game. The mindset of a person determines how a person chooses their strategy in order to get what they want. Alice and Bob both like each other after the date, but they spend about 4 days to confirm the status of their relationship. Think about if they both texted each other immediately after the date, they could have both confirmed their feelings towards each other and became a couple immediately after the first date. However, this is not always the case in real life since we do not know how the other person is thinking. A rational person always tries to be safe and avoids unfavorable situations. In the case of dating, being too eager in a relationship might scare the other away.
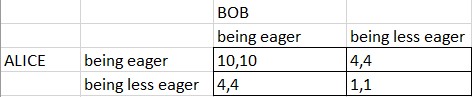
If we construct a payoff matrix according to their situation, we can see that Alice and Bob are facing the Prisoner’s dilemma. Since both of them do not want to seem eager to each other, they both have a lower payoff. This means that they spent unnecessary time on playing mind games with each other (represented as (1, 1) in the payoff matrix) to reach the same result had they both chosen “being eager” (to start communicating immediately after the date). We can see that this scenario illustrates a breakdown of communication between Alice and Bob. The lack of cooperation and overly considerate behavior between the two leads to a situation very similar to the Prisoner’s dilemma, and they do not really have a dominant strategy since they cannot know what the other is thinking. If they talk openly, maybe they would end up in a better Nash equilibrium of (10,10), but not (1,1) (Figure 2).
In conclusion, dating apps are a modern way to meet people and find your love. However, people tend to be cautious when they pursue people that they like, which creates such a situation that might result in one very similar to the Prisoner’s dilemma.
References:
- https://fee.org/articles/coase-theorem-the-prisoner-s-dilemma-and-zero-sum-games-in-modern-dating/
- https://qz.com/996851/why-we-need-a-dating-app-that-understands-nashs-equilibrium/
- https://generic.wordpress.soton.ac.uk/meetingofminds/2018/03/22/game-theory-matching-apps-as-social-networks/
- https://www.britannica.com/science/game-theory/The-prisoners-dilemma