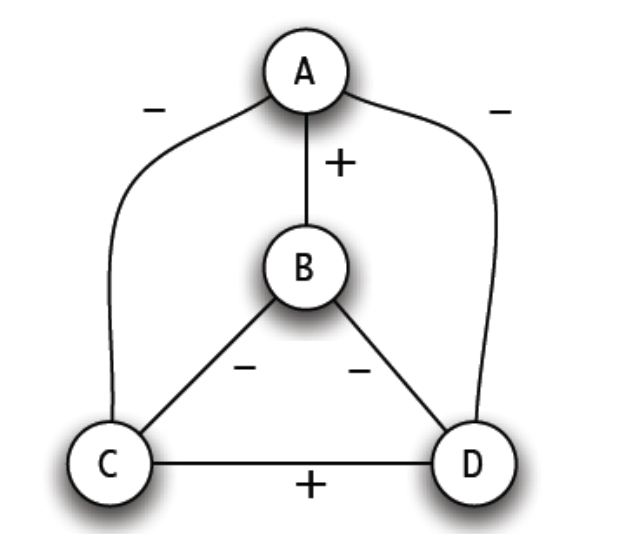
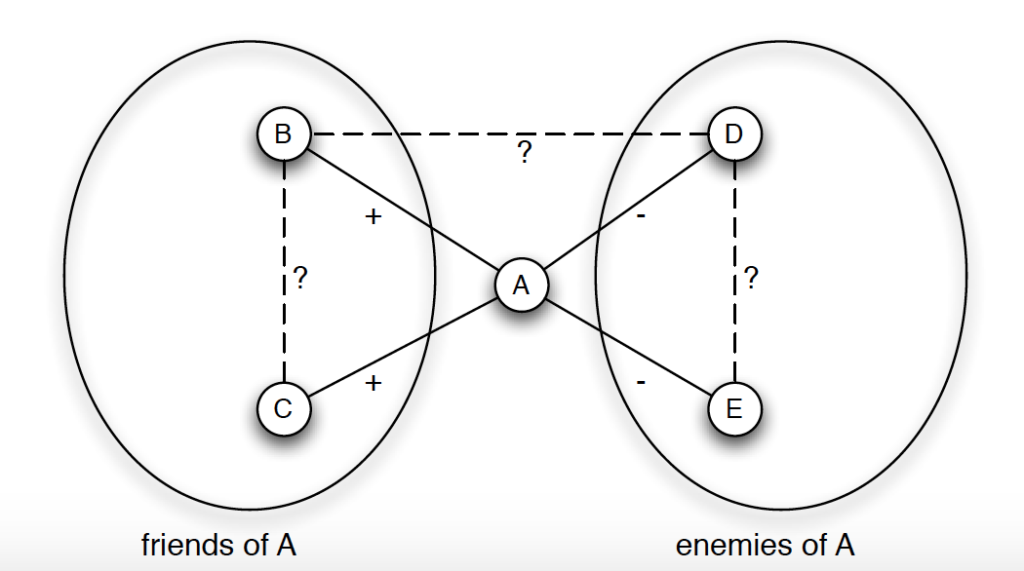
Many years have passed since we have been introduced to the concept of social media, and as 2019 is nearing its end, it has already been 15 years since Facebook has first launched. By now, it should be no surprise that most of us are revealing more personal information to the public than we would have in a world with no social media, or that Facebook is able to get even more data about you than you have ever intended to reveal. Looking back, how has social media impacted the world of politics? The article ‘What Facebook Did to American Democracy’ attempts to put all the pieces together, introducing personality profiling data1.
I’m sure by now, anybody who has used Facebook must have seen (seemingly innocent) online quizzes that ask you for completion to share its results with your friends. This is actually one example of harvesting data by means of psychographic profiling. With such information, users can be divided and then grouped into networks (as we have seen in class). An ethical way to use such data would be to expose to you targeted advertisements, but it can also be used in ways that influence your stance in politics. Through the harvested data, specific political messages are targeted to different segments without anybody realizing; “How does a campaign know what its opponent is saying if ads are only targeted to white Jewish men between 28 and 34 who have expressed a fondness for U2… and who donated to Barack Obama’s campaign?”2 Harvested data can also be used to target you with posts that you want to see; “Pariser … noticed conservative people, whom he’d befriended on [Facebook] despite his left-leaning politics, has disappeared from his News Feed… no conservative links for me.”2
Targeted political messages to communities. Users targeted only by posts that align with their stance. Adding these together, we have a network where a platform (such as Facebook) provides a source of information (targeted messages), all while eliminating and preventing other sources of information (filtered/targeted posts). In essence, we get communities who’s members have strong ties with each other, with few to none weak edges between the communities.
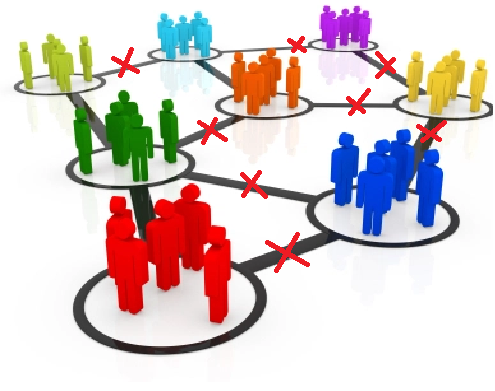
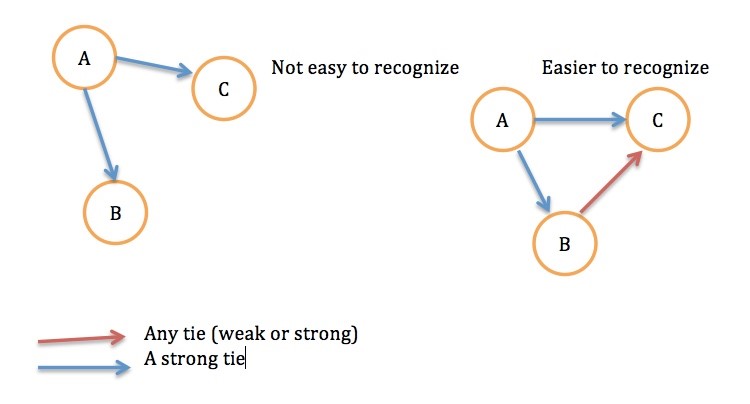
Taking into consideration Granovetter’s explanation of the social and structural role of an edge, the lack of weak edges prevents communities from accessing other sources of information. Couple this with other tactics involving media (such as blowing up fake news3 ), and we can see that large platforms like Facebook have the power to affect the general population’s stance in politics.
References:
(1) Facebook is Killing Democracy with its Personality Profiling Data. Timothy Summers https://theconversation.com/facebook-is-killing-democracy-with-its-personality-profiling-data-93611
(2) What Facebook Did To American Democracy. Alexis Madrigal –https://www.theatlantic.com/technology/archive/2017/10/what-facebook-did/542502/
(3) Heres Why Facebook’s Trending Algorithm Keeps Promoting Fake News. Craig Silverman – https://www.buzzfeednews.com/article/craigsilverman/can-facebook-trending-fight-off-fake-news#.fadKm1WOG
Image: https://ourpangea.files.wordpress.com/2012/04/social-networks.jpg?w=584