The Internet of Things(IoT) is a system relying on physical devices which, collecting information and sharing those information through the internet without any human efforts. Thanks to cheaper chips and the great power of internet, billions of physical devices around the world are able to be connected to the internet, as a result, IoT becomes more efficient.
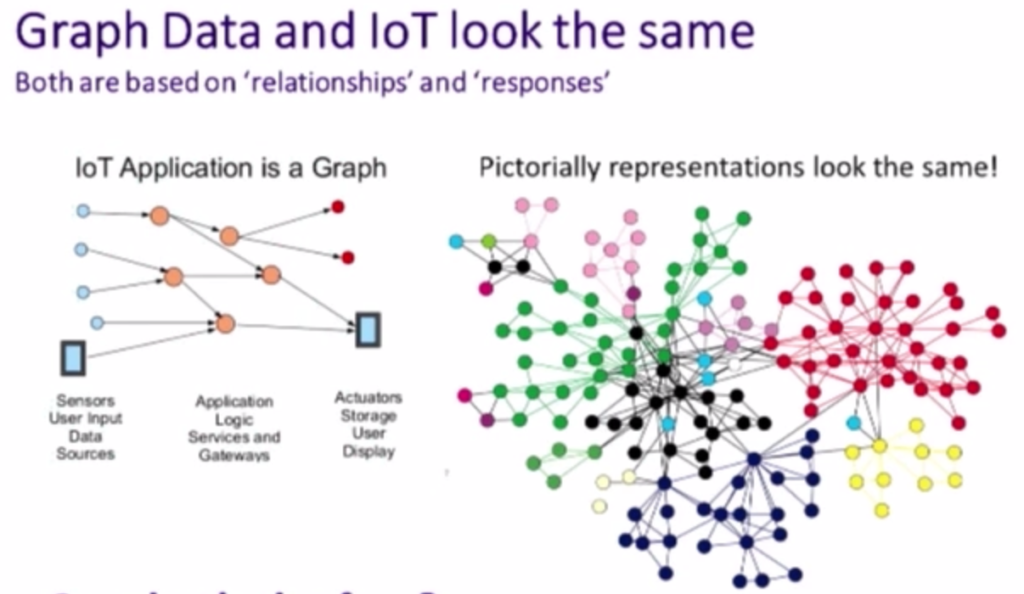
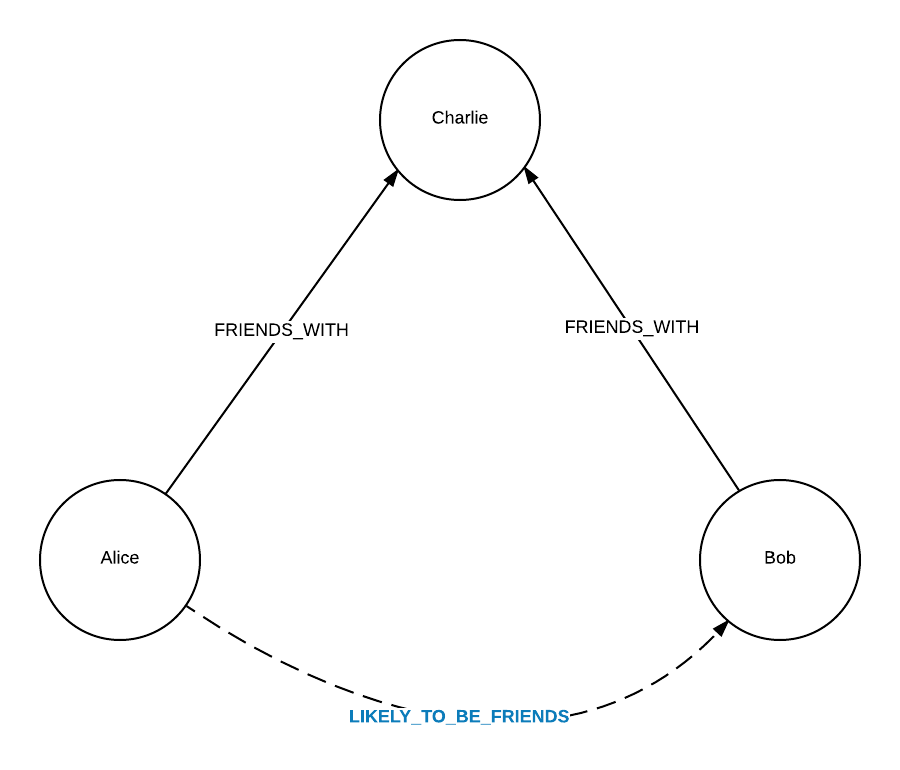
The network constructed by the IoT devices looks like the graphs above, and it has many paths inside the network. Every path starts from the user input data(data sources) and passes the application logic services and gateways(intermediate nodes). Finally, the information in the network reaches the storage and display stage (upper-level nodes). Overall, it is evident that IoT creates a network developed by hardware devices in an effective way. Since it does not require any manual work, it speeds up the transmission of information.
Some of my concerns is whether the fast-speed IoT be a potential threat to the public’s privacy and whether the information in the network is recorded without the public’s permission. The fact is that sensors in the network will collect some extremely sensitive data such as what you say and do in the private space. However, as many IoT devices cannot be patched effectively, they have become the target of many hackers. The hackers are now able to get private information from the device level, and the users’ information security is put in the weak position.
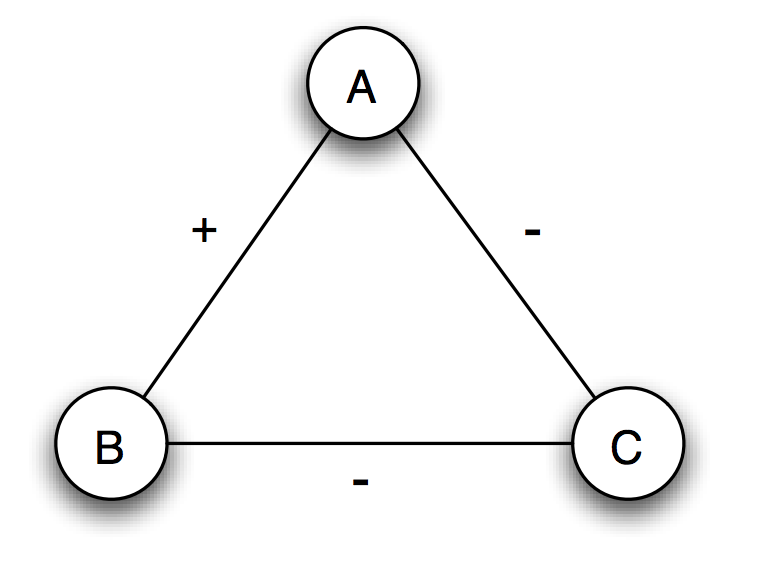
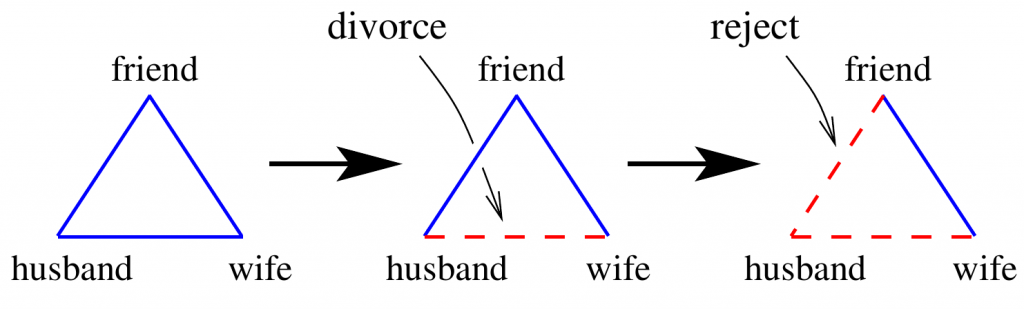
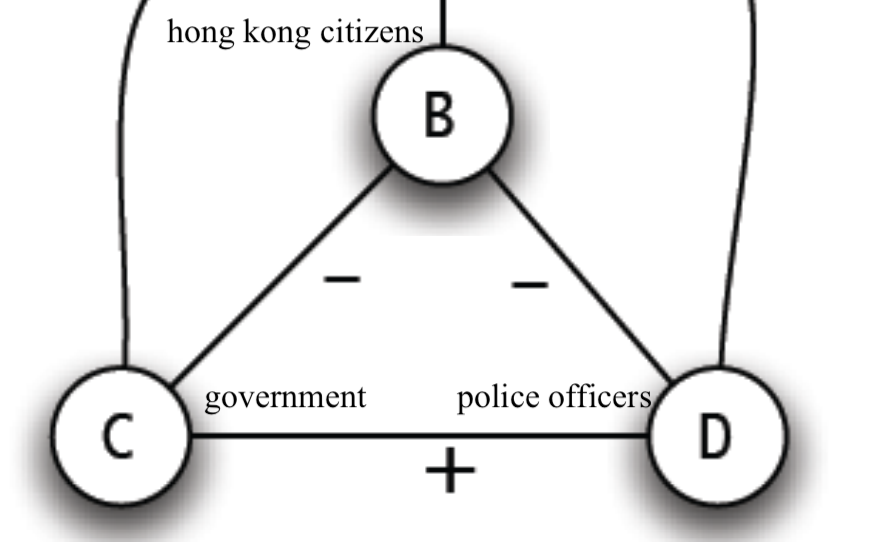
One of the ways that we express the relationship (of what)is like the graph above. Node B represents the user and Node C represents the IoT device. Node B does not trust Node C since IOT wants to record some parts of data and keeps the privacy. By the theory of structural balance, in order to keep the whole network balanced, we need to find another node A which can be another device, another person to be trusted or another group (decentralized).
At present, people think about combining the blockchain technology with the IoT to increase privacy security. The advantage of blockchain is that the block will be broadcasted to many parties to get the validation of information before adding it to the chain. The third parties works in the same way as node A which I want to find out previously. After the information gets validated, it is safe to go released.
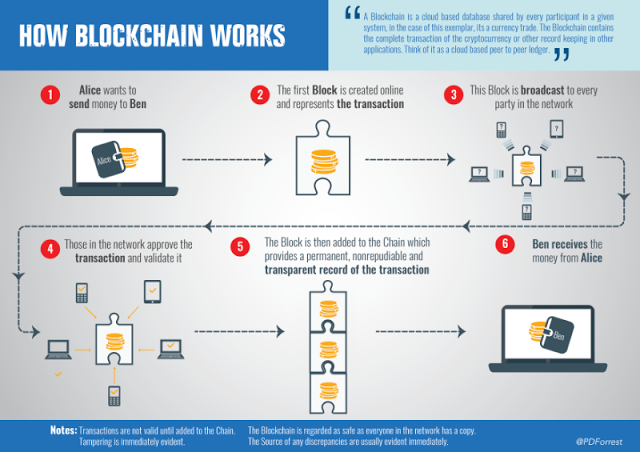
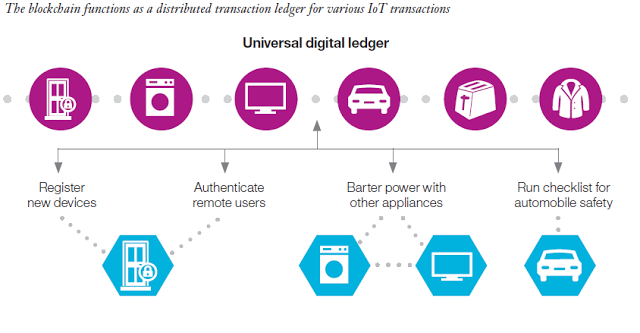
IoT still has a few problems currently, but in the near future, these problems are likely to be solved since the public and the market pay much attention on it. Hopefully, IoT can be integrated into people’s life and can be applied in the business system someday.
References:
https://datafloq.com/read/securing-internet-of-things-iot-with-blockchain/2228
https://neo4j.com/blog/iot-graphs-business-requirements/ https://innovationatwork.ieee.org/blockchain-iot-security/