With technology in the world becoming increasingly critical in our lives, the importance of security across the platforms we use are also becoming incredibly crucial to improve. Game Theory is already being used today in order to predict an attacker‘s method of stealing information from a defender.
The idea discussed in the article utilizes Game Theory, considering a game where a player (the attacker) needs to steal information from the second player (the defender). With this setup – we can create contradictory incentives, and allow these models to compete with each other. Through the process we can analyze and model the security problems the attacker’s invade, and the security measures the defenders construct. Furthermore, this setup allows for multiple players, and up to hundreds of thousands of scenarios before deciding an action, in order to fully explore the capabilities each player has to offer, and even more-so simulate what a real attacker would do in the real world. In each scenario the payoff is considered for each action, based on the likelihood of success, and the risk of getting caught by the defender. Below is a simple diagram representing the decision network that the attacker and defender use in order to make their decisions:
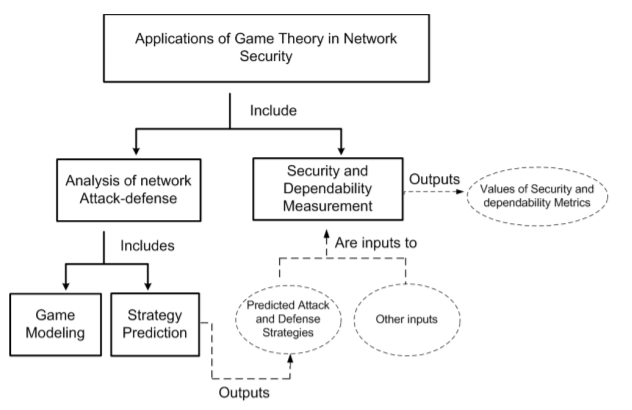
The article further dives into details about the strategy prediction, utilizing fictitious plays – which are essentially fake scenarios created either by the attacker of the defender in order to predict what they will do, and how to overcome/prevent such an event. The article also discussed cooperative game models, for scenarios where the attacker may need to steal information from other players who are on the same team (such as from a company with many users who are all actively trying to prevent an attack). In this case the attacker might single-out a weak link with few security measures, or come up with some other scenario with a high payoff.
In conclusion, a Game Theory approach to solving network security as a whole would never be sufficient. However, the ability to consider hundreds of thousands of scenarios is an extremely powerful tool that should be utilized to its fullest potential in the industry. As network security continues to evolve, it is important that as many scenarios are considered as possible in order to protect personal and otherwise critical data.
http://yangxiao.cs.ua.edu/IEEE_COMST_game_2013.pdf
Liang, X., & Xiao, Y. (2012). Game theory for network security. IEEE Communications Surveys & Tutorials, 15(1), 472-486.