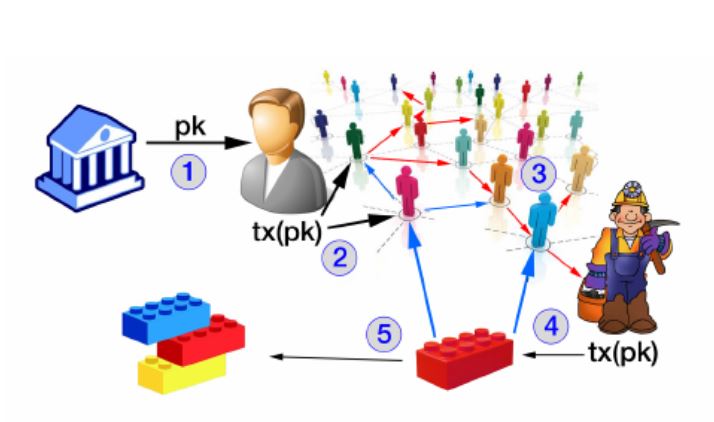
In computer and networking security course we learned about the communication and interactions between the user and servers via OpenPGP, which intrigued me to research about graph theory and the network properties of these communication relationships. The trust in openPGP nowadays relies on social relations for identify verification; ideally a web of trust should model real world relationships.
OpenPCP consist of two main subcategories PGP and GPG.
Pretty good privacy, also known as PGP is a way for people to communicate over the internet, protected from eavesdropping. This technology is used in everyday communication such as emails and messages. The idea of PGP is consisted of both a public and a private key for each user. Where messages are encrypted with the receiver’s public key, only the receiver can decrypt the message using their private key; there for ensures no one else other than the receiver can get the message.
OpenPGP is the newer version of PGP that is capable for international use. Where the certificate is verified by finding a trustworthy certification path to an already verified key, meaning all verified certificates are linked to one and other in some way. Every user using OpenPGP will be generating a public/private key that becomes the certificates to verify each other. The generated keys are stored in a Synchronizing Keyservers (SKS) for later referencing.
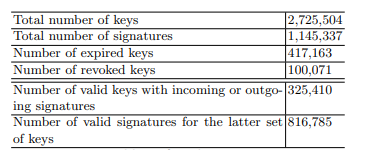
This table is the overall data set that was gathered in 2009 about 2.7 million keys found in the key database storing key transactions within OpenPGP. Within that data there is one signature chain between every key pair that forms strongly connected components (SCC). The signature chain is the connection between all keys that are trusted. A key become trusted after a already existing trustworthy key accepts this new key.
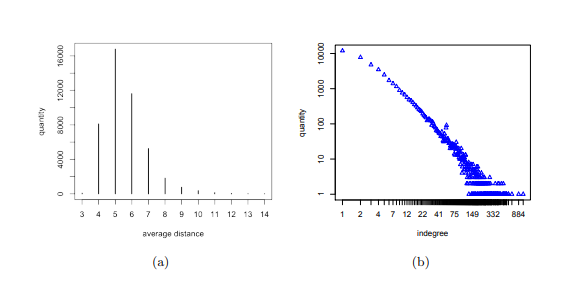
Graph (a) is the average distances between nodes (keys) in a log-log degree scale from the table above. Meaning the distribution of the node degrees (number of keys) follows a power law distribution. In the graph (a), the largest SCC range is between four and seven. The certification path for GPG must be no longer than 5 keys. So the average of graph (a) is slightly below the GPG limit. Further indicating that the OpenPGP is as powerful as the usage of the GPG. Graph (b) shows the indegrees in the largest SCC, which shows the result to be heavily skewed, which a much higher average. The keys in OpenPGP show a impeccable example of large data and degree distributions.
GPG also known as GnuPG is branch off of OpenPGP, where it serves as a replacement for PGP. In the basic concept of GPG follows closely to the structural Balanced/unbalanced Network we studied in class. GPG uses a decentralized trusted model, where it branch out to other trusted source; similar to the motto “friend of my friend is my friend”. Identical to the theory of structural balance, where the edges of the structural triangles are all positive is consistent with “friend of a friend” intuition.

This is the case with trusted interaction processed by the GPG forms a balanced network. On the other hand, the unreliable sources can also be processed by GPG and form a balanced network. This is followed by the intuition that “the enemy of my friend is my enemy”. In GPG, if a user A or a source A is flagged to be untrustworthy by some trusted source B, then the untrustworthy source A will become untrustworthy to the sources that believe the trusted source B. Therefore forming the balanced structure, where all trusted source distrust the malicious source A. GPG is a perfect example of a balanced structure in a large network.
The relationship of online interactions and the trust between each user is quite intriguing and heavily related to what we have learned in Social and Information Networks course. From something that we use every day, in the background of all our communication on the internet, is importantly associated to some of the most important network properties.
Ulrich, A., Holz, R., Hauck, P., & Carle, G. (2011). Investigating the OpenPGP Web of Trust. Computer Security – ESORICS 2011 Lecture Notes in Computer Science, 489-507. doi:10.1007/978-3-642-23822-2_27
[Schematic diagram of a Web of Trust]. (n.d.). Retrieved November 12, 2020, from https://en.wikipedia.org/wiki/Web_of_trust#/media/File:Web_of_Trust-en.svg