In order for hackers to attack a corporation, they must first find a method to gain access to the corporation’s LAN. This can be done by phishing certain individuals within the organization and getting access to their workstation. However, that individual may not have enough privilege in the organization and their account cannot access the information sought after by the hacker. At this point, they must make use of the account they acquired in order to try to hack into an account with higher privileges.
To find accounts with higher privileges, a viable method is identity snowball attack or derivative local admin attack. This method uses the account they have acquired, and scan for other users on the network. Afterwards, a random user is picked as the pivot and the process continues until the desired domain admin account with all the necessary rights is found. The problem with this method is that it is possible to arrive at dead ends where the account does not give any further access. In this case, it is necessary to go back to the previous user, scan the network, and repeat the process again. So the problem with this method was that it takes a lot of time and especially larger organizations.
There is a much better way to perform such attacks using graph theory. It would be wise to construct a graph that illustrates the relationships between the users, their admin rights, and group delegations. An application called BloodHound was developed to do so. A graph can be constructed, giving the user an understanding to the network structure, and then algorithms from graph theory such as Dijkstra’s can be used to calculate the shortest attack path. Using the graph constructed, BloodHound‘s application allows for Cypher queries to be run in order to determine a user’s admin rights, group memberships and more. As a result, a lot of blind guessing-and-checking is omitted and a lot of time is saved for hackers.
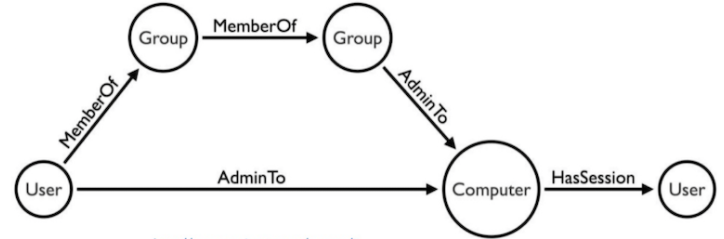
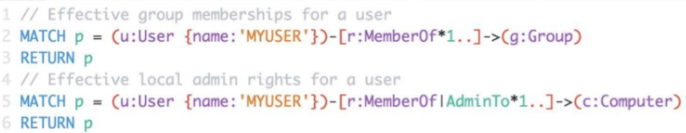
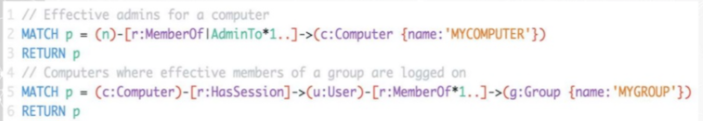
In conclusion, graph theory allows for hackers to represent the relations between users under a network in a meaningful way that allows them to model their organization’s network and plan their attack path according to the traversal of the graph. This method is much quicker compared to identity snowball attack. Additionally, this realization introduced efficient Attack Path Automation such as ANGRYPUPPY and GoFetch. These projects takes the results outputted from BloodHound and automates the attack, making hacking much easier and efficient.
Source: https://neo4j.com/blog/bloodhound-how-graphs-changed-the-way-hackers-attack/
ANGRYPUPPY: https://github.com/vysecurity/ANGRYPUPPY
GoFetch: https://github.com/GoFetchAD/GoFetch