An interesting game theory that displays the bystander effect is the Volunteer’s Dilemma. This game models a scenario where there are two or more players. A player in the game can make a small sacrifice to benefit everybody, or do nothing and hope that someone else will make that sacrifice for them. When nobody does anything, there is a negative consequence for everyone.
The payoff matrix for each player could look like this:
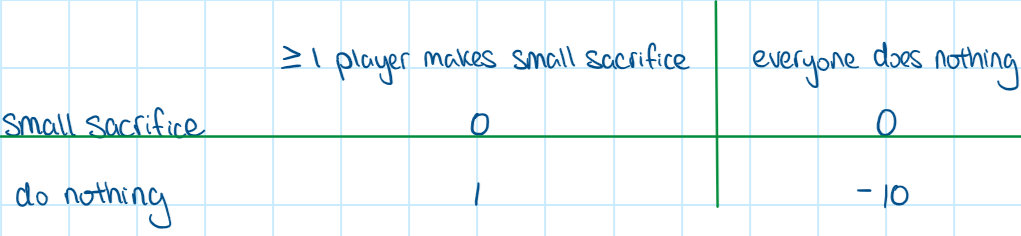
It is obvious that there is no pure strategy Nash equilibrium. However, there is a mixed strategy equilibrium which indicates that the probability of one person making a small sacrifice will decrease as the amount of players that participate in the game increases. Analyzing this game model explains the bystander effect in real life where people are less likely to make a sacrifice or help in a situation when there are other people around.
Volunteer’s Dilemma has occurred in real life situations such as the murder of Kitty Genovese in 1964. There were 38 witnesses that saw or heard the murder but chose to ignore it and not contact the authorities. This murder got a lot of attention and led to the discovery of the bystander effect and also this game theory.

Another example of the dilemma can also be found in wildlife within a group of meerkats. When a group of meerkats is searching for food, there is a small group that is assigned to act as guards and keep watch of the area. That group is supposed to let out a warning call for the rest of the meerkats when they spot danger in the wild. However, doing so can put themselves at risk. It is obvious how the volunteer’s dilemma occurs within the group of meerkats that act as guards. Any of the meerkats letting out a warning call would result in everyone being informed of the dangers, and all of the guarding meerkats choosing to do nothing and run away would result in all the other meerkats to be caught by surprise.
In conclusion, game theory can be used to model and explain a lot of results and actions taking during real life situations similar to Volunteer’s Dilemma and also Prisoner’s Dilemma covered in lecture.
Sources:
http://people.virginia.edu/~cah2k/vg_paper.pdf
https://www.psychologytoday.com/ca/blog/media-spotlight/201604/exploring-the-volunteers-dilemma
http://greenteapress.com/complexity/html/thinkcomplexity015.html