This year, Paul Milgrom and Robert Wilson have won the 2020 Nobel Economics Prize for their important contributions to auction theory and inventions of new auction formats that we are using today.
Now let me introduce auctions with some examples:
Let’s say you know that a burger usually costs $10 at McDonald’s, and you are very hungry at the moment. But would you go to MacDonald’s and directly tell the cashier that you are willing to pay more for a burger since you are hungry? No. Because your hunger is private information to you only, you would rather get the food at the regular price.
What happens if this time you are the food seller? Would you ever tell the customer the minimum price of a burger you are willing to sell when you know it will sell more than the minimum price? You wouldn’t. Because that’s private information to you again.
A classic situation of an auction happens when you are competing with several other buyers, then the seller would prefer to sell the limited item to the buyer with the highest bid. Under this situation, each buyer will gradually reveal his/her highest private value that he/she is willing to pay to win the auction item.
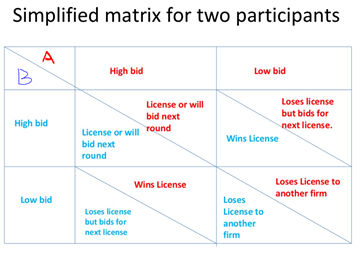
Private information makes auctions interesting. From the perspective of game theory, no one would know the exact payoffs from the strategies that bidders made since the private values are very subjective to each of the bidders. So, what should bidders do? With the question in mind, Milgrom and Wilson started the research to analyze how different bidders behave strategically when they each have access to different information during auctions. In 1969, Wilson recognized that the Nash equilibrium concept would permit an analysis of auctions with common value, meaning that part of the auction item’s true value is equal to all potential bidders while having the other part as the different private values.
Private and common values in auctions also lead to a well-known phenomenon called “the winner’s curse”. That is, the winner wins the auction only when his/her bid is higher than anybody else. This indicates that the winner’s bid may exceed the true value of the item a lot which ends up in a loss on the transaction.
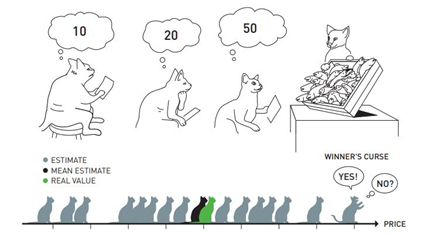
Therefore, how to make a wise choice in an auction that balances the risks and the probability of winning the auction is always a challenging topic. And hopefully, with the knowledge of game theory, we can find out the best strategies in every “auction” in our life.
References: